In an era where businesses increasingly rely on third-party vendors and service providers, managing third-party risk has become a critical component of organizational resilience. Organizations must ensure that their partners maintain robust controls to protect sensitive data and operations. One of the most recognized ways to demonstrate such controls is through SOC certification. Understanding how SOC certification contributes to third-party risk management is vital for businesses seeking to reduce vulnerabilities and build trust across their supply chain.
The Growing Importance of Third-Party Risk Management
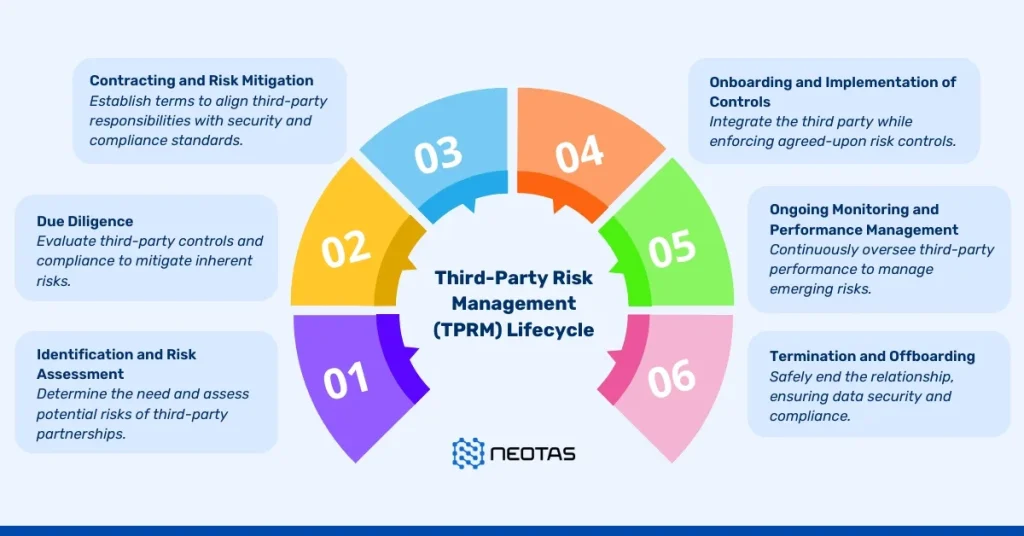
Third-party risk management (TPRM) refers to the processes organizations use to identify, assess, and mitigate risks associated with external vendors and partners. These risks range from data breaches and operational disruptions to compliance violations and reputational damage.
As companies outsource more functions—from IT services to payroll processing—the potential for risk exposure grows. Third parties often have access to sensitive customer information, proprietary data, or critical systems. Without effective oversight, a weak link in the supply chain can become an entry point for cyberattacks or cause regulatory compliance failures.
Therefore, businesses need reliable indicators of a third party’s control environment. This is where SOC certification plays a pivotal role.
What is SOC Certification?
SOC, which stands for System and Organization Controls, refers to a series of auditing frameworks developed by the American Institute of Certified Public Accountants (AICPA). These certifications provide standardized assurance reports on an organization’s internal controls related to security, availability, processing integrity, confidentiality, and privacy.
The two most common SOC reports used in third-party risk management are SOC 1 and SOC 2:
- SOC 1 focuses on controls relevant to financial reporting.
- SOC 2 evaluates controls related to security and data privacy.
Organizations undergo rigorous audits conducted by independent certified public accountants (CPAs) to obtain SOC certification. The resulting reports offer detailed insight into how well the organization’s controls meet the defined criteria over a specified period.
How SOC Certification Supports Third-Party Risk Management
SOC certification provides organizations with credible, standardized evidence that their third-party vendors maintain strong control environments. This transparency is invaluable when assessing potential partners and monitoring ongoing risk.
First, SOC reports help reduce the need for duplicative audits. Rather than conducting separate, costly assessments for every vendor, businesses can rely on the findings documented in SOC certification reports. This streamlines due diligence processes and accelerates vendor onboarding.
Second, the level of detail and rigor in SOC audits offers businesses confidence in the third party’s operational effectiveness. For example, a SOC 2 report provides assurance around security controls designed to prevent unauthorized access or data leaks. This helps organizations evaluate whether a vendor meets their risk tolerance levels.
Third, SOC certification facilitates ongoing monitoring. Many SOC reports are issued periodically, offering up-to-date information on controls. Businesses can incorporate SOC report reviews into their third-party risk management programs, quickly identifying emerging risks or lapses in controls.
Integrating SOC Certification into Risk Assessment Frameworks
Effective third-party risk management integrates multiple sources of information, including contract terms, cybersecurity questionnaires, and independent assessments. SOC certification acts as a key input within this framework.
Risk teams can categorize vendors based on the scope and type of SOC certification they hold. For critical vendors handling sensitive data, a SOC 2 Type II report demonstrating operational controls over time may be required. Less critical vendors might only need SOC 1 or Type I reports, which offer point-in-time assessments.
Reviewing the scope of the SOC audit is equally important. Organizations should ensure that the certified controls align with their specific risk concerns, such as data privacy or availability.
SOC reports also serve as a basis for follow-up actions. If a report identifies control exceptions or recommendations, businesses can require remediation plans or enhanced monitoring for that vendor.
Enhancing Compliance and Regulatory Confidence
Many industries operate under strict regulatory requirements concerning data security and privacy. Regulators increasingly expect organizations to exercise due diligence in managing third-party risk.
SOC certification helps demonstrate compliance with these expectations. For example, financial institutions under the oversight of the SEC or FINRA often require SOC reports as part of vendor risk assessments.
By incorporating SOC certification into third-party risk management, organizations can provide regulators with documented evidence of their control evaluation processes. This reduces audit findings related to vendor management and strengthens overall compliance postures.
Addressing Limitations and Complementing SOC Certification
While SOC certification is a powerful tool, it is not a silver bullet. SOC reports focus on specific control criteria within defined scopes and timeframes. They do not guarantee that no risk exists or that all controls are perfectly implemented.
Therefore, SOC certification should be viewed as part of a broader third-party risk management strategy. Businesses must complement SOC reviews with ongoing monitoring activities, contract negotiations that specify security requirements, and incident response planning.
Additionally, organizations should be aware of the type of SOC report they receive. Type II reports offer more comprehensive assurance than Type I, which only assesses controls at a single point in time.
Real-World Examples of SOC Certification in Vendor Management
Consider a technology company selecting a cloud service provider. A SOC 2 Type II certification from the provider assures the company that the cloud service operates effective security controls over several months. This assurance influences contract negotiations and allows the company to focus on integration rather than extensive audits.
In another scenario, a healthcare organization requiring HIPAA compliance might prioritize vendors with SOC 2 reports covering confidentiality and privacy criteria. This helps meet regulatory obligations while protecting patient data.
These examples illustrate how SOC certification simplifies risk assessment and fosters trust between businesses and their partners.
Future Trends in SOC Certification and Third-Party Risk
The evolving cybersecurity landscape and increasing regulatory scrutiny continue to elevate the importance of SOC certification in third-party risk management.
Emerging trends include the integration of SOC reports with automated risk management platforms. This allows continuous analysis of vendor controls alongside other risk indicators.
There is also growing interest in expanding SOC frameworks to cover areas such as cloud security and supply chain resilience, reflecting the complex ecosystems organizations operate within today.
Businesses that stay current with SOC certification developments and incorporate them effectively into risk management programs position themselves to manage third-party risks proactively.
Conclusion:
Managing third-party risk is an ongoing challenge requiring transparency, rigor, and collaboration. SOC certification provides a trusted, standardized method to evaluate and monitor the control environments of vendors and service providers.
By integrating SOC certification into their third-party risk management processes, organizations gain credible assurance, reduce audit overhead, enhance compliance, and build stronger business relationships.
While SOC reports are not a standalone solution, they form a critical pillar in a comprehensive approach to mitigating risks arising from complex vendor ecosystems. Businesses that leverage SOC certification strategically are better equipped to safeguard their operations, data, and reputation in an interconnected world.